Employment Background Screening Basics for Hiring Managers
With around 96% of companies conducting some type of employee background screening during their hiring process, according to a report by the Society...
With Verified Credentials' mobile-first candidate experience, you meet candidates where it's most convenient. Learn how easy we make it.
|
|
Now offering DOT services!Get your drivers on the road quickly and meet DOT regulations. |
Gain clarity about your compliance responsibilities with our new Adverse Action Guide! Use the interactive map to learn what regulations apply in your area.
Verified Credentials is a leading background screening company. Since 1984, we’ve helped validate and secure relationships through the use of our comprehensive screening solutions. We offer a wide variety of background checks, verifications, and innovative screening tools.

Our accreditation confirms that our policies, processes, and employee training meet rigorous industry compliance standards.
3 min read
Verified Credentials Sep 21, 2022 12:00:00 AM

When screening new candidates, employers collect a significant amount of private information. With most of this critical data stored digitally, protecting it can be challenging. Especially when compared to the physical paper files of the past.
Having an effective data security protocol is key to ensuring that sensitive information does not become available to outside parties. Let's look at what employers may consider keeping data secure.
Access to candidate information may be on a need-to-know basis. To maintain data privacy, employers may enact and follow certain protocols diligently. Your team may determine user roles and groups to clarify:
This could help establish clear rules as to who should and should not be able to access critical data, mitigating the opportunity for a data breach.
Do you have a vast number of departments or hiring categories? You can keep data even more secure by extended criteria without feeling limited. Verified Credentials allows clients to create unlimited user groups and profiles, providing the freedom to set up a variety of specific parameters based on your unique needs. Your system administrators can even set up, change, and assign users without our help.
It's also important to determine when a user no longer needs access. This could be either because their role has changed or perhaps they have left the organization. How long since the last login will the user remain active?
Also crucial to your platform’s success is considering password policies. A common approach is to use advanced password requirements requiring a certain alpha-numeric password length. Likewise, a system may require 2-factor authentication, which still requires users to sign in with a password. However, then the system sends an authentication link to the user’s established email address or phone number. Consider which policy may work best for your users while offering the security you need.
Also significant is the number of login attempts allowed. Are users allowed three tries before being locked out of an account and having to contact an administrator? Consider how this might impact your background check process and user experience. You may also choose to add other filters to limit access to specific IP addresses.
To have a holistic approach to data security, it’s essential to understand who has access to your stored data. That includes those that work for your screening partner. These individuals must be carefully selected within the organization based on the need of their role. It is important to confirm they are appropriately vetted and trained.
Background checks are already a standard course for most hiring processes. This should extend to screening company employees who will have access to this sensitive information. Beyond administrative protections, physical security should also be provided. This includes on-site data center security to ensure limited, secure access to housing locations.
What other policies might a screening company have? Data encryption is important for any sensitive information that may transfer digitally. Once data is obtained, you may want to ensure it is adequately encrypted in transit and at rest to ensure its protection.
The information gathered during a background check represents some of the most fundamental data an individual can carry. Protecting it is one of the most important tasks a company can do. Verified Credentials has the tools and experience to help ensure every piece of private information gathered is protected and safe.
Our Information Security Management System (ISMS) aligns with NIST 800-53 security controls. Our ISMS standard is like HITRUST and ISO 27001 measures. They are all different frameworks for data security with some overlap, and NIST ranks among the most comprehensive. This means you can rest assured that we design our systems to protect your sensitive data.
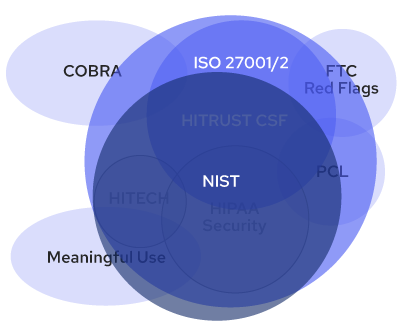
In the world of IT data security, there are multiple types of standards a company can align with to establish an ISMS standard. Each is different, but you can see that NIST is one of the most expansive and thorough ways to protect sensitive information.
Our mission is to keep personal information private and secure. We do this by operating with the strictest information handling and technology practices.
You already know the importance of protecting sensitive background data. Rest assured, Verified Credentials works to keep critical information secure. We provide reliable solutions to help you manage and store secure data you gather during a background check. We vet and train our staff to follow the strictest standards in data security.
Contact us to learn how Verified Credentials provides efficient solutions you can count on to help manage your sensitive data.

With around 96% of companies conducting some type of employee background screening during their hiring process, according to a report by the Society...

If you oversee Tuberculosis (TB)testing for current employees and candidates, you know how important it is to keep the process running smoothlyand...

Many industries rescreen their staff on a regular basis, whether annually or periodically. As organizations look to get 2026 off to a strong start,...

It’s no secret that connecting all human resources processes in one convenient ecosystem is the gold-star goal for many HR leaders. The efficiency...

At Verified Credentials, we have all departments housed under one roof. Everyone working together in the same place means we can walk down the hall...
![Believe It When You See It: Signs of an Effective Background Check [PART 2]](https://blog.verifiedcredentials.com/hubfs/Imported_Blog_Media/Blog_Standard%20image%20-%20periwinkle-Oct-07-2024-05-25-52-5447-PM.png)
In part one of our series discussing visible signs of effective background checks, we highlighted how itemized invoices might indicate the overall...